Depending on your configuration, users can be authenticated via KeyShield SSO. For automatic authentication is necessary to install KeyShield SSO client on station.
Instructions for unattended installation are at KeyShield_server/static/kshield_msi.page. For manual installation/configuration please follow screenshots:
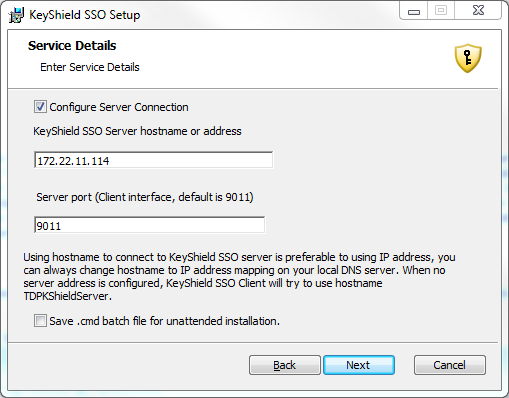
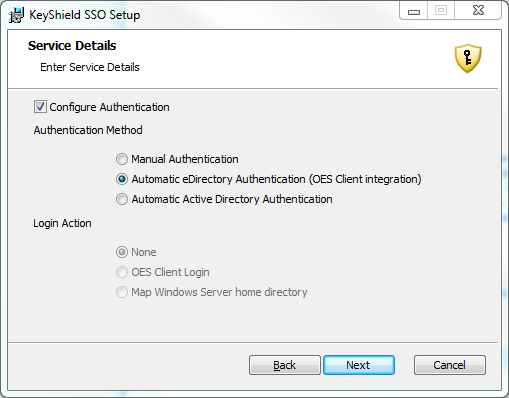
The OES client for Windows integration works in a similar manner like former ClientTrust for BorderManager – KeyShield server creates a token and stores it as a value of attribute of the user’s object. KeyShield client reads the value through the OES client for Windows API, uses it as a challenge, generates a response and sends it to the KeyShield server. Then the KeyShield server validates it and if OK, accepts the client authentication request and sends confirmation back to the client. Client changes color of the icon in the task bar to green in order to inform the user that authentication is done. Here is the related setting in the related eDirectory connector of the KeyShield server (keep in mind, you can use as many eDirectory trees, AD forests, etc. as you need at the time).
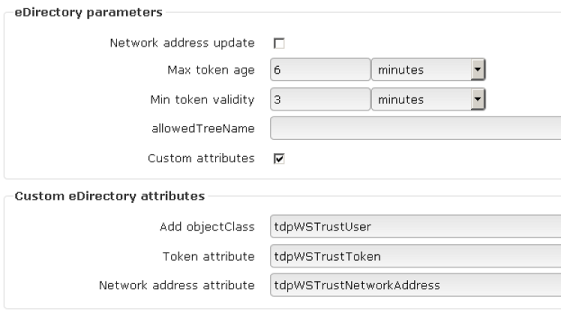
This is so called custom setup but it is not necessary. The best practice is to let the KeyShield server to configure eDirectory connector automatically by choosing.
First enter Connector ID and provide LDAP server IP and port
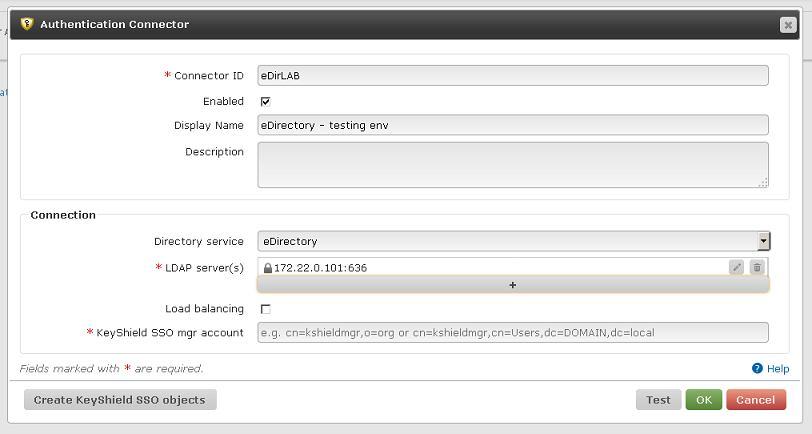
Then click “Create KeyShield SSO objects”
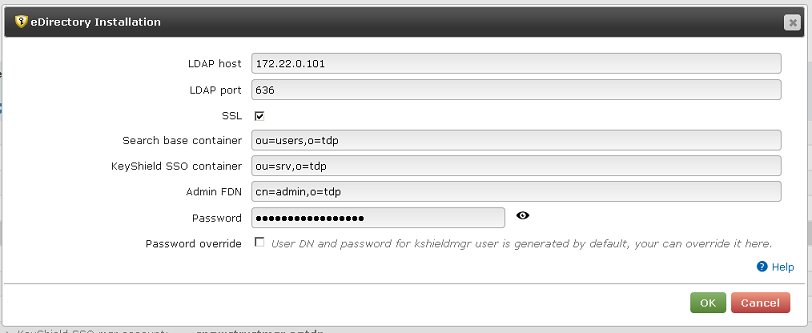
KeyShield SSO will create own mgr account (proxy account used to access eDirectory), extend schema by auxiliary class (can be removed) for tokens and assign minimum access rights the mgr account needs.
Once you are done with this setting, the automatic authentication with the OES client for Windows should work. If not, consult Diagnostic log.




